
CRPR Help
Introduction
The CAVS Restricted Project Repository (CRPR) is a system designed to house restricted and controlled project documents and
deliverables with access for both researchers and sponsors. This system serves multiple projects from multiple sponsors and is
a restricted system with access strictly controlled.
Security Requirements
With the presence of unclassified but controlled information (ITAR/Export Controlled), the CRPR system must meet the security standards
stated in the DFARS 252-204-7000 “Safeguarding Covered Defense Information and Cyber Incident Reporting" (Oct 2016) clause, and the
associated NIST SP 800-171 security guidelines and requirements. In order to meet these standard requirements, certain security restrictions
are placed on the CRPR system.
The CRPR system utilizes a Microsoft Sharepoint server to manage the repository. In order for Sharepoint to be complaint with security standards and requirements, a new user account management module was developed to provide the needed password security and authentication methods. Native Sharepoint password security and authentication methods do not meet and are not compliant with the DFARS/NIST standards stated above.
In order to further secure the data made available by the CRPR system, there are firewall restrictions in place based on IP addresses that block access to the system and only allows those addresses that are cleared and approved through to the system.
As part of the security standards, CRPR utilizes Two Factor Authentication (2FA) to allow the user to access the system. 2FA adds an additional layer of security for the system. 2FA is discussed in further detail below.
The CRPR system utilizes a Microsoft Sharepoint server to manage the repository. In order for Sharepoint to be complaint with security standards and requirements, a new user account management module was developed to provide the needed password security and authentication methods. Native Sharepoint password security and authentication methods do not meet and are not compliant with the DFARS/NIST standards stated above.
In order to further secure the data made available by the CRPR system, there are firewall restrictions in place based on IP addresses that block access to the system and only allows those addresses that are cleared and approved through to the system.
As part of the security standards, CRPR utilizes Two Factor Authentication (2FA) to allow the user to access the system. 2FA adds an additional layer of security for the system. 2FA is discussed in further detail below.
System Design
The repository design is based on the original SimBRS Sharepoint system, though it is NOT the original Sharepoint system. The main
difference on the design is that it is now expandable to meet the needs of other projects outside of SimBRS with improved security.
With access to the CRPR system being controlled at the firewall, new users who need an account cannot reach the CRPR system to register. Therefore, CRPR is a split system: the restricted repository and an open-accessible account management system.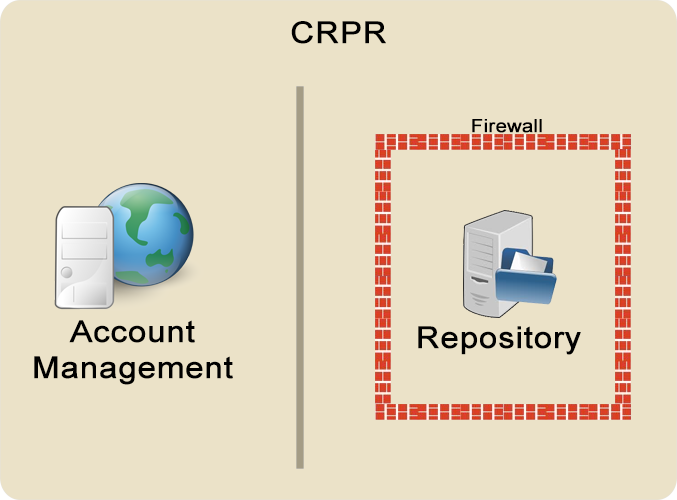 The CRPR System is a split system with two modules. The first module is the account management module. This module is open to access
from the public and it handles everything dealing with the user’s account. This module provides an interface to allow new users to
register for an account; provides tools to help a user who forgets their username or password, needs to change their password, or
needs to set up their Two Factor Authentication; and is used for account activation. The address to the account management system is
https://www.cavs.msstate.edu/crpr.
The CRPR System is a split system with two modules. The first module is the account management module. This module is open to access
from the public and it handles everything dealing with the user’s account. This module provides an interface to allow new users to
register for an account; provides tools to help a user who forgets their username or password, needs to change their password, or
needs to set up their Two Factor Authentication; and is used for account activation. The address to the account management system is
https://www.cavs.msstate.edu/crpr.
The second module is the actual repository. Once the user is approved and given access through the firewall, they can go to the repository. If the user does not need to manage their account, then they can go straight to the repository. The address for the repository is https://crpr.cavs.msstate.edu.
With access to the CRPR system being controlled at the firewall, new users who need an account cannot reach the CRPR system to register. Therefore, CRPR is a split system: the restricted repository and an open-accessible account management system.
 The CRPR System is a split system with two modules. The first module is the account management module. This module is open to access
from the public and it handles everything dealing with the user’s account. This module provides an interface to allow new users to
register for an account; provides tools to help a user who forgets their username or password, needs to change their password, or
needs to set up their Two Factor Authentication; and is used for account activation. The address to the account management system is
https://www.cavs.msstate.edu/crpr.
The CRPR System is a split system with two modules. The first module is the account management module. This module is open to access
from the public and it handles everything dealing with the user’s account. This module provides an interface to allow new users to
register for an account; provides tools to help a user who forgets their username or password, needs to change their password, or
needs to set up their Two Factor Authentication; and is used for account activation. The address to the account management system is
https://www.cavs.msstate.edu/crpr. The second module is the actual repository. Once the user is approved and given access through the firewall, they can go to the repository. If the user does not need to manage their account, then they can go straight to the repository. The address for the repository is https://crpr.cavs.msstate.edu.
Logging into the System
Since the two modules of CRPR are located on different systems, they cannot share the same login. If the user logs into one
module, they will be asked to log in again when accessing the other. Once the user is set up with access, they can go directly
to the repository and bypass the account management system altogether. The login pages for both modules provide links that point
the user to the other module.
The login process is the same no matter which module the user is trying to log in to. The user will provide their username and password followed by their 2FA PassCode.
The login process is the same no matter which module the user is trying to log in to. The user will provide their username and password followed by their 2FA PassCode.
Failed Login Attempts
The system logs failed login attempts for a user. On the seventh failed login attempt within a certain amount of time, the
system will lock the user’s account. Once an account has been locked, the user will not be allowed to log in to the system
until the lock is cleared by system administrators.
Two Factor Authentication
The CRPR system utilizes a Two Factor Authentication process (2FA) to allow users to log in to the system. 2FA increases
the security of the login process and better ensures that the account being logged in to belongs to the person trying to
log in. The 2FA system utilizes the Time-based One-Time Password (TOTP) protocol.
Each implementation of 2FA is different from other implementations as each defines a unique pass-phrase that the 2FA codes are built on and cannot be shared with other implementations. That is why the MSU 2FA is different from the HPC2 2FA and they are not interchangeable. The HPC2 implementation of 2FA is for use by HPC2 account holders only and cannot be used for CRPR as half the users are not HPC2 account holders. Therefore, CRPR has its own 2FA implementation.
The CRPR system provides 2FA by one of three methods:
Each implementation of 2FA is different from other implementations as each defines a unique pass-phrase that the 2FA codes are built on and cannot be shared with other implementations. That is why the MSU 2FA is different from the HPC2 2FA and they are not interchangeable. The HPC2 implementation of 2FA is for use by HPC2 account holders only and cannot be used for CRPR as half the users are not HPC2 account holders. Therefore, CRPR has its own 2FA implementation.
The CRPR system provides 2FA by one of three methods:
- Via Email (default) - A 2FA PassCode is generated and sent to the registered email address. This PassCode is then provided in the login process. PassCodes via email are valid for 30 minutes.
- Via Text - A 2FA PassCode is generated and sent as a text message to the registered cell number. This PassCode is then provided in the login process. When the user sets up 2FA to work via text, they will provide their cell information. PassCodes via text are valid for two minutes.
- Via App - A PassCode is generated via an app on a smart device. This PassCode is then provided in the
login process. No communication is needed between the CRPR system and your smart device. Just open your app, take the PassCode
given to you, and provide it to the login process when asked. PassCodes via apps are valid for one minute.
There are several apps available that you can use for free that support the Time-based One-Time Password (TOTP) protocol. The most popular one is Google Authenticator. Duo can also be used for your CRPR 2FA, as well as other apps that are built by Microsoft, Yahoo, Apple, and etc. To set up your app to provide the correct PassCode for CRPR access, a QR code is provided for the app to scan. The QR Code is unique to the user, so it can't be used for someone else to log in.
Account Inactivity
The CRPR System monitors activity on the system. Users who have no activity with their account within a three month period will
have their account automatically locked. Once locked, the user will not be able to log in to the system until the lock is
cleared by system administrators.
Account Registration
The registration process starts with the user filling out the registration form. The user will provide their information as
accurately as possible. The user’s email is used for communication throughout the registration process and with the user
activating their account. Therefore the user should take great care to ensure the information provided is correct. The user must
provide specifically what access they need within the system.
As part of the registration process, the user must provide information about their IP address that they will be using to access CRPR. The user’s system being used to access CRPR must be compliant with the security standards listed above.
Users accessing the CRPR from within the CAVS networks already have their IPs allowed and do not have to provide their IP information.
If the user’s system is behind a proxy, on a private network, or is currently connected to a public access internet (ex. airport/hotel internet), the IP being reported by their system might not be the correct IP that is needed. The user should consult with their system administrators for assistance to determine the proper IP to use.
Users can find their IP address from a "Command Prompt" window on a Windows machine. To open a "Command Prompt" window, click the start menu and select the "Run" tool. When the "Run" box appears, type in "cmd" and click "OK".
If the "Run" option is not there, the user can type "cmd" into the "Search programs and files" box within the start menu. This should show an option for "cmd.exe" that the user can select. The user can find assistance via Google if needed.
In the command prompt window, type "ipconfig" and enter. The IP address will be the complete number listed as "IPv4 Address".
Other methods in finding your IP address can be found from Microsoft through Google.
Some systems utilize DHCP which assigns a machine a random IP address. If the user’s system gets an IP address through DHCP, they can consult with their system administrators to get a static IP assigned to their system, or the user will need to provide a range of IP addresses. A static IP is preferred. In each case, the user will need to consult with their system administrators for assistance.
The registration process continues as the new registration is reviewed for approval. If approved, the appropriate access is set up and the user is sent an email to activate their account. To activate their account, the user will log in using their username and password they provided during the registration process. However, since the user has not set up their 2FA, they will not be asked for a PassCode during activation. Once logged in, they will provide their activation code.
After the user activates their account, they will have an opportunity to set up their Two Factor Authentication. 2FA defaults to using email for the login process. The user will be able to change their 2FA at any time.
As part of the registration process, the user must provide information about their IP address that they will be using to access CRPR. The user’s system being used to access CRPR must be compliant with the security standards listed above.
Users accessing the CRPR from within the CAVS networks already have their IPs allowed and do not have to provide their IP information.
If the user’s system is behind a proxy, on a private network, or is currently connected to a public access internet (ex. airport/hotel internet), the IP being reported by their system might not be the correct IP that is needed. The user should consult with their system administrators for assistance to determine the proper IP to use.
Users can find their IP address from a "Command Prompt" window on a Windows machine. To open a "Command Prompt" window, click the start menu and select the "Run" tool. When the "Run" box appears, type in "cmd" and click "OK".
If the "Run" option is not there, the user can type "cmd" into the "Search programs and files" box within the start menu. This should show an option for "cmd.exe" that the user can select. The user can find assistance via Google if needed.
In the command prompt window, type "ipconfig" and enter. The IP address will be the complete number listed as "IPv4 Address".
Other methods in finding your IP address can be found from Microsoft through Google.
Some systems utilize DHCP which assigns a machine a random IP address. If the user’s system gets an IP address through DHCP, they can consult with their system administrators to get a static IP assigned to their system, or the user will need to provide a range of IP addresses. A static IP is preferred. In each case, the user will need to consult with their system administrators for assistance.
The registration process continues as the new registration is reviewed for approval. If approved, the appropriate access is set up and the user is sent an email to activate their account. To activate their account, the user will log in using their username and password they provided during the registration process. However, since the user has not set up their 2FA, they will not be asked for a PassCode during activation. Once logged in, they will provide their activation code.
After the user activates their account, they will have an opportunity to set up their Two Factor Authentication. 2FA defaults to using email for the login process. The user will be able to change their 2FA at any time.